Category: Proxies
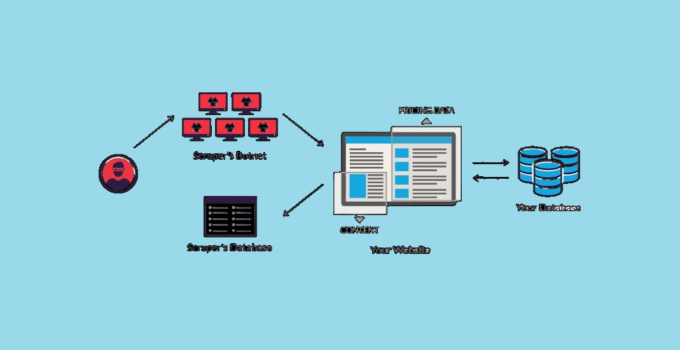
With the exponential growth of information available online, extracting structured data from websites at scale has become increasingly common. Companies now utilize automated software programs known as web scrapers …
VPN and Proxy are two terms that are often used interchangeably, but they are not the same thing. Both VPN and Proxy can be used to hide the user’s …
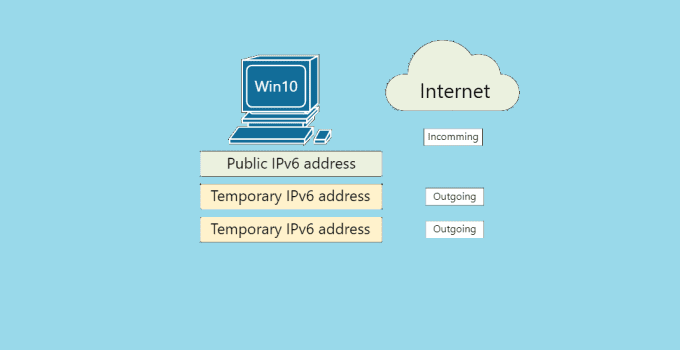
IPv6 (Internet Protocol version 6) is the most recent version of the Internet Protocol, the communications protocol that provides an identification and location system for computers on networks and …
An IP also known as (Internet Protocol) address is a unique identifier assigned to every device connected to the Internet. This IP allows your devices to communicate with each …
The long-term health and stability of your application depend on regular monitoring. By using a reliable monitoring system, you may resolve issues more quickly and uncover possible performance problems …
Forward proxy and reverse proxy servers are two types of proxy servers used to secure communications between two networks. These two types of proxy servers are differentiated in the …
Browsing the internet anonymously has become increasingly sought after by the average user and for good reason. Between data tracking, location tracking, and advertising, maintaining privacy online can be …
In today’s digital world, robust proxies are essential for protecting your data and identity. Each form of proxy has its own strengths and weaknesses and can be used to …
API testing automation is a vital component of modern software development. It has various benefits, such as quicker test execution, improved test coverage, and the potential to detect errors …
It’s no longer a question of why you should secure your online identity but how. Even if you aren’t doing anything suspicious or illegal, all websites are tracking you …