Category: Cyber Security
With the enormity of challenges facing organizations today, new and sophisticated cyber threats like ransomware can be easy to overlook. Yet at their own peril. Ransomware has proven to …
The security service edge (SSE) is a new cloud-native architecture that delivers integrated security services to distributed enterprise networks. SSE platforms integrate multiple network security functions like secure web …
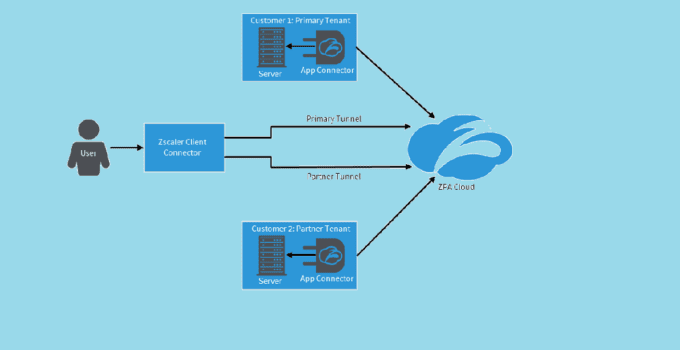
The Zscaler Client Connector is a lightweight software agent that enables secure and smooth access to internal applications and resources for remote employees. Part of the Zscaler Zero Trust …
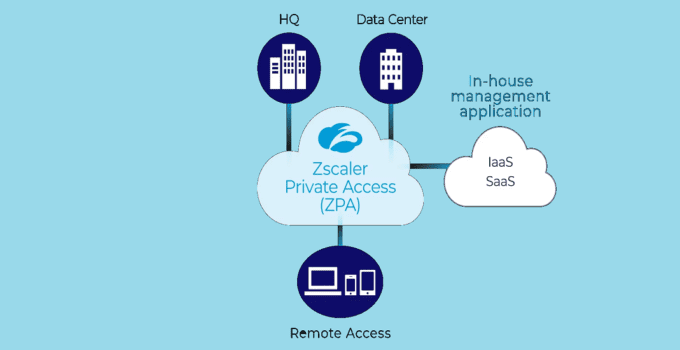
Zscaler Private Access (ZPA) is a cloud service that provides secure remote access to internal applications and resources without bringing users directly on the corporate network. ZPA works by …
Remote browser isolation (RBI) has become an increasingly important cybersecurity technology in recent years. As more business is conducted online, organizations must find ways to protect themselves and their …
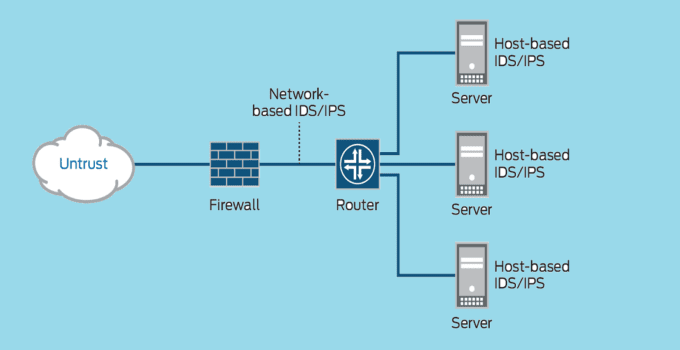
What Is Intrusion Detection and Prevention System? (IDPS). An Intrusion Detection and Prevention System (IDPS) is an essential security tool that monitors networks and systems for malicious activity and …
Privacy engineering has become an increasingly important discipline within the broader field of cybersecurity. As data breaches and privacy scandals continue to make headlines, companies and organizations are recognizing …
FitGirl Repacks is a well-known name in the world of video game piracy. Essentially, FitGirl is an individual or group known for compressing video games into smaller file sizes, …
SMS Peeper is presented as an application that supposedly enables users to read someone else’s text messages without their knowledge. There is considerable debate surrounding its effectiveness and whether …
Hashing and encryption are two common methods used in cryptography to protect data. While related, they serve different purposes and have some key differences. This article will provide an …